When Encrochat was hacked it wasn’t as simple for the police to find the users as you may believe, like tracing phone numbers for example would be pointless because a handsets didn’t have numbers, they also didn’t allow phone calls – only pictures and texts could be sent on the so called encrypted phones.
This made it difficult for police to locate the users and they relied heavily on suspects revealing details like street names and photographs that could be used to find and arrest them.
In this recent case a drugs trafficker helped investigators smash his own organised crime group by sending a photograph of his dog on encrypted communications platform EncroChat showing his partner’s phone number on the animal’s tag.
Danny Brown, 55, operated on EncroChat under the handle ‘throwthedice’.
He sent an image of his pet, named ‘Bob’, to co-conspirator Stefan Baldauf, 62, as they worked on a plot to send 448 kilos of MDMA worth £45m to Australia.

National Crime Agency investigators zoomed in on the phone number and used it – among many other tactics in a painstaking investigation – to prove Brown was part of the conspiracy.
Bob was present when Brown was eventually arrested.
Brown and Baldauf also sent accidental selfies of themselves on Encrochat – giving investigators more proof they were involved in the plan, which saw the drugs hidden in the arm of an industrial digger and shipped to Australia.
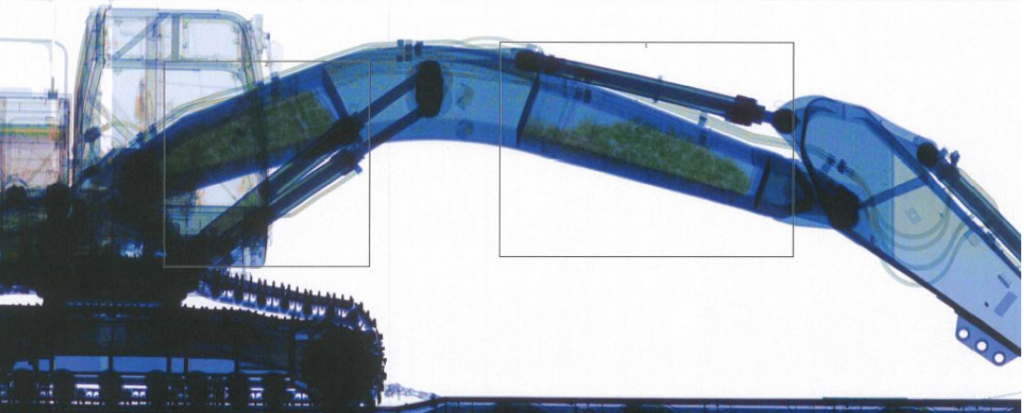
The OCG members sent the 40-tonne Doosan digger down under on the pretence of selling it.
They organised an online auction to make the excavator’s arrival in Australia look legitimate. But they rigged it by agreeing a pre-arranged bid with the intended recipients.
The auction provided the OCG a nervous moment when other potential buyers registered their interest in the digger.
OCG member Leon Reilly, 50, messaged Brown on EncroChat: “There are six people watching it.”
Brown replied: “F***ing hell, that’s not good is it.”
Brown, Baldauf and Reilly were convicted in June at Kingston Crown Court of drugs trafficking with three other men.
Today, Brown was jailed for 26 years, Baldauf for 28 and Reilly for 24.
The trio and their conspirators plotted in late 2019 and early 2020 to send the drugs, which were 77.5% pure, to Australia where MDMA’s street value is much higher than in the UK.
EncroChat was taken down in 2020.
The NCA led Operation Venetic – the UK law enforcement response to the takedown – which provided investigators with messages offenders had sent thinking the platform was safe from global law enforcement attention.
EncroChat users’ real names did not appear on phone messages – instead, they all used a ‘handle’ which investigators needed to attribute to real world suspects.
In one message, Brown, of Kings Hall Road, Bromley, Kent, sent a photo to his crime group of his television which showed his reflection in it.

And Baldauf, of Midhurst Road, Ealing, London, sent a picture of a brass door sign with his face visible in the reflection.
The OCG bought the excavator, a Doosan DX420, for 75,000 Euros.
Reilly, who used a UK address of Tudor Way, Hillingdon, Uxbridge, but was from Dunbeacon in Bantry, Co Cork, Ireland, arranged for the digger to be moved from Leeds by his company ‘Mizen Equipment’.
The digger was safely housed in an industrial unit in Grays, Essex.
Accomplice Tony Borg, 44, of Southwark Path, Basildon, Essex, took delivery of the machine at an industrial unit in Grays, Essex, and worked on it.
Philip Lawson, 61, of Wraysbury Road, Staines-upon-Thames, designed the hide and arranged a welder to cut open an arm of the digger and seal the Class A behind a lead lining.
Lawson bought a powerful welding machine and arranged for a sign-making company to make some stickers to cover the markings once it had been repainted.
It is believed the drugs were hidden inside the digger on 19 December 2020.
In the days before and after, the OCG members’ Encro phones were in frequent contact with each other and also used the same cell sites at certain times.
Mizen Equipment paid a haulage firm £1,600 to move the digger to Southampton Docks and it took from 24 January to 13 March to arrive in Brisbane, Australia.
Australian Border Force officers x-rayed the digger, removed the drugs, sealed the arm and installed a tracker and listening device before letting it move onto its intended destination – an auction house in Sydney.
The digger was moved to a small site west of Sydney in May 2020 and Lawson forwarded the Australian OCG a drawn diagram of exactly where the drugs were hidden and how the digger should be opened.

